Non-Employee Risk Management
Identity-first partner access
Secure, streamline, and govern how business partners access your systems and data.
Challenge & solution
Simplify and secure partner onboarding
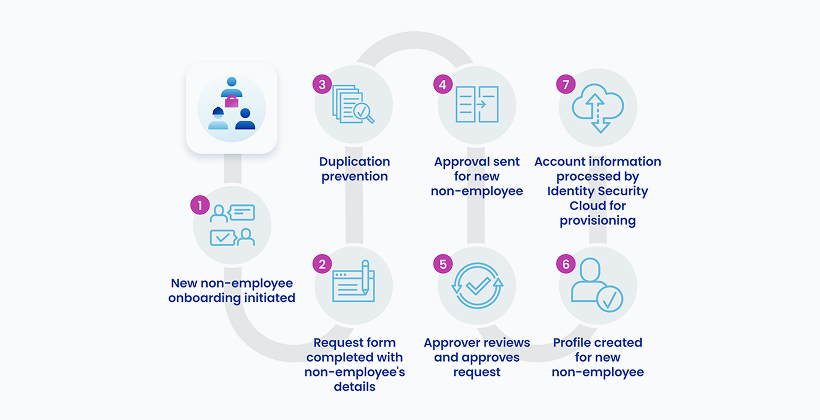
Business partners often operate outside traditional HR systems—making onboarding slow and risky. SailPoint Non-Employee Risk Management replaces manual processes with secure, connected workflows.
Disconnected onboarding processes
Managed through spreadsheets, emails, and tickets
Owned by business, not IT or identity teams
Delayed access impacts revenue-generating activities
Manual processes create audit and security risk
Streamline partner onboarding
Automates provisioning through secure, policy-based workflows
Enables collaboration between identity, IT, and business teams
Delivers timely access aligned to partner roles and risk
Provides a scalable, auditable system for third-party governance

Webinar
Strengthen supply chain security
Explore how enterprises are improving security and scalability in their supply chain by modernizing third-party onboarding with SailPoint's Non-Employee Risk Management.
Benefits
Make business partner access faster and safer
SailPoint Non-Employee Risk Management scalable lifecycle management for every stage of the partner journey—onboarding, extension, offboarding, and rehiring. Eliminate risky workarounds, reduce delays, and gain visibility and control over partner access
Accelerate onboarding
Faster time to partner productivity
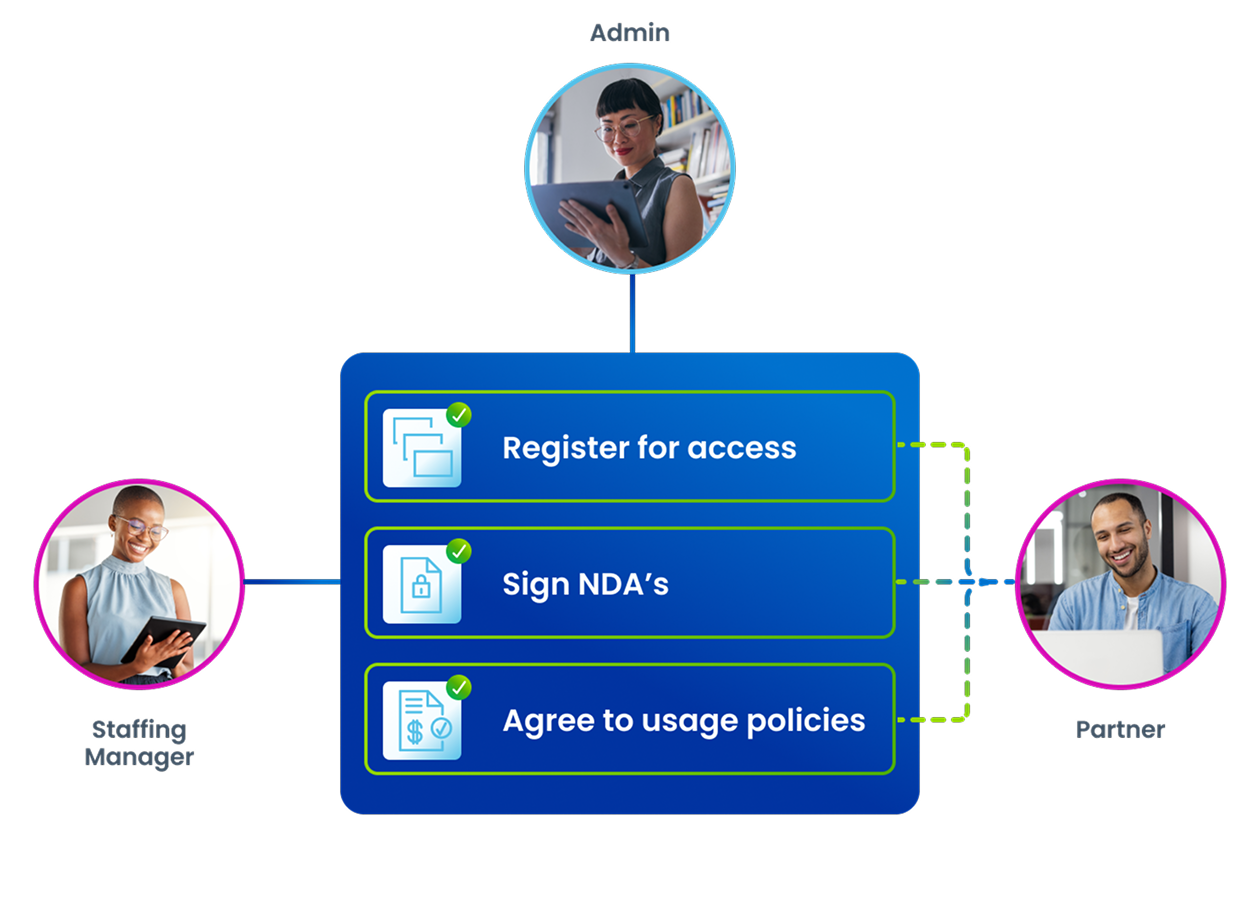
Simplify onboarding with secure collaboration portals that enable both internal teams and external partners to actively participate in onboarding and ongoing identity management. This shared access model improves data accuracy, strengthens accountability, and reduces the administrative burden on your team.
Advanced Capabilities
Take your identity security solution even further
The SailPoint Identity Security Cloud delivers the essentials for most organizations. SailPoint also offers advanced capabilities for specific needs.
Business partner access
Secure external access at scale
Affiliates, agents, and vendors need access fast—but manual processes create risk. See how industries secure third-party access without slowing business down.
Manufacturing & supply chain
Secure and manage access for logistics providers, plant contractors, and supply chain partners across global operations.
Learn moreInsurance
Manage access for agents, brokers, and third-party administrators—without relying on risky, manual onboarding processes.
Read insurance white paperHigher education
Secure access for adjunct faculty, research collaborators, and third-party vendors—while maintaining compliance and protecting student data.
Read moreRelated resources
Discover more third-party security insights
faq
Frequently asked questions
Who qualifies as a business partner in identity security?
A business partner is any external user or organization that requires access to your internal systems, applications, or data but is not managed through your HR system. This includes franchisees, agents, brokers, suppliers, and service providers. Because these non-employees often operate outside standard identity workflows, managing their access can be complex without a dedicated third-party identity lifecycle management and governance solution.
Can we control what business partners have access to…and for how long?
Yes. With SailPoint Non-Employee Risk Management, you can control business partner access based on their role, relationship, and the systems they need to interact with. As responsibilities change or projects end, access can be updated, extended, or removed instantly. This ensures that each partner only has access to what’s necessary—helping reduce over-provisioning and improving your overall security posture.
What happens if a partnership ends or access needs to be removed quickly?
When a partnership ends or a user no longer requires access, all associated access can be terminated immediately with a single action. Non-Employee Risk Management gives you centralized visibility and control over business partner identities, helping prevent orphaned accounts and reducing third-party security risk across your environment.
Can we onboard large groups of business partners efficiently?
Absolutely. SailPoint supports bulk onboarding capabilities for business partners and other third-party users. This makes it easy to upload and configure multiple external identities at once, assign appropriate access levels, and apply governance policies consistently, saving time and reducing manual effort.
How does this improve audit and compliance for partner access?
Non-Employee Risk Management provides an audit trail of every business partner’s identity, access level, owner, and certification status. This helps you maintain compliance with regulatory requirements and internal policies by demonstrating exactly who had access to what, when, and why—all in one centralized system.
How does Non-Employee Risk Management support identity verification for business partners?
SailPoint Non-Employee Risk Management integrates with leading identity verification providers to verify the identities of business partners during onboarding. Whether you're working with agents, contractors, or franchisees, identity verification helps ensure that the person requesting access is who they claim to be—reducing the risk of impersonation, fraud, and unauthorized access. This is especially important when granting access to sensitive systems or data across distributed partner networks.
How does this solution support business and IT collaboration?
Non-Employee Risk Management enables business users to participate in onboarding and access requests through intuitive collaboration portals, while IT and identity teams retain full control and visibility. This collaborative model speeds up access delivery and ensures governance policies are applied consistently across all third-party identities.