Non-Employee Risk Management
Extend identity security to third parties
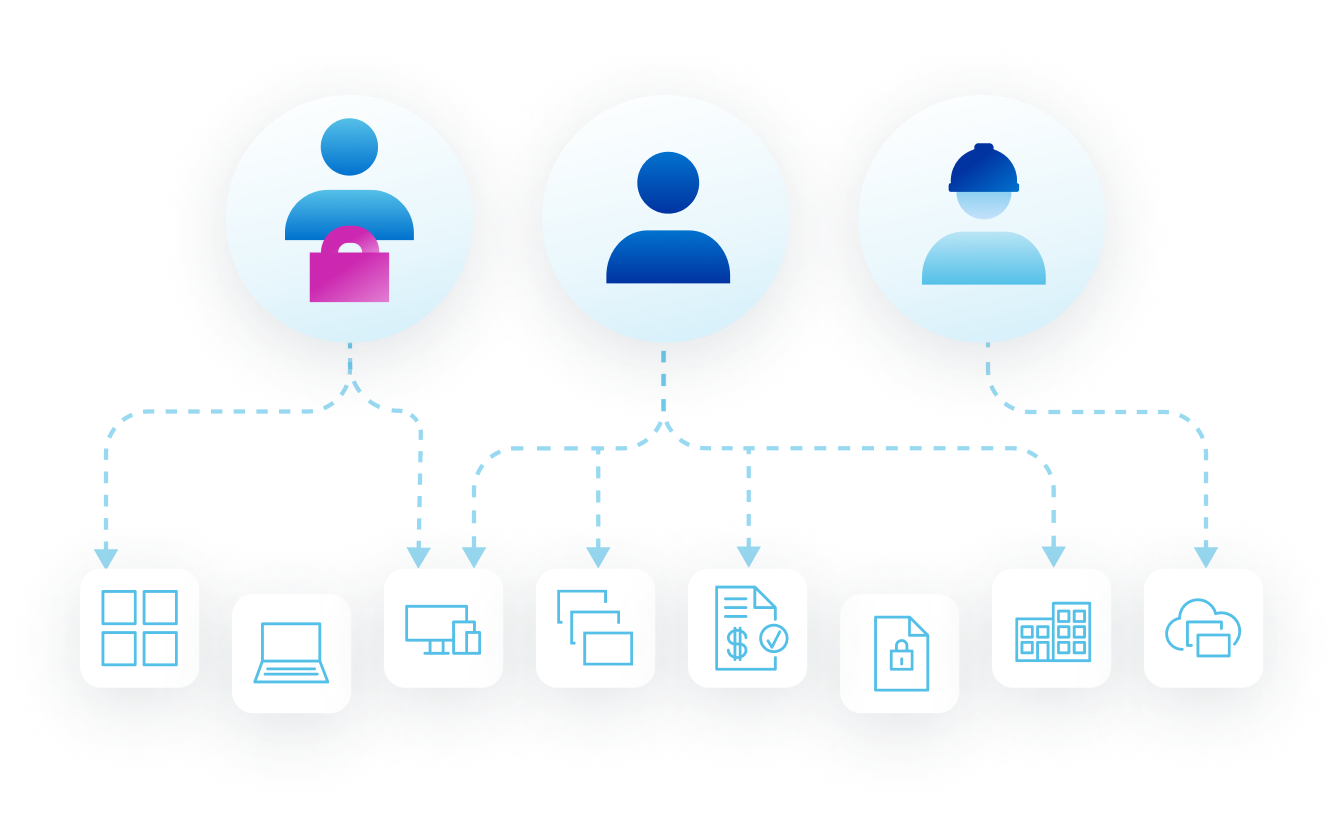
Non-Employee Risk Management secures your external identities—contractors, business partners, vendors, and more—through processes tailored to how your business operates.
Challenge & solution
Secure third-party access from day one
Third-party identities often bypass governance, leading to risk, blind spots, and compliance gaps. Bring them into your governance framework—securely, at scale, and aligned to your business.
Non-employee access is messy
Disconnected onboarding processes make it hard to collaborate across internal and external teams.
Inadequate oversight of third-party access leads to risk, audit issues, and compliance gaps.
HR tools weren’t built for non-employees—and manual workarounds (spreadsheets, emails, tickets) don’t scale securely.
Without controlled business processes, third-party identities lack ownership, context, and lifecycle control.
Smarter non-employee security
Empower teams and partners to securely onboard non-employees—enhancing data accuracy and reducing manual effort.
Get insight into your non-employees and their access, verify identities during onboarding, and proactively identify risky access to improve your security posture.
Eliminate manual workarounds with a scalable system purpose—built for non-employee lifecycle management, including role changes, new project assignments, and extended end dates.
Govern third-party identities with complete context—who they are, why they have access, and when it should end.

Strategic capability
Featuring verified identity support
Non-Employee Risk Management integrates with leading identity verification providers to deliver secure, standards-based verification for third-party identities. Onboard faster—and with greater confidence.
Use cases
Purpose-built for third-party risk
Non-Employee Risk Management brings structure and control to external identity governance, solving blind spots and challenges your current tools can’t address.

Simplify and secure business partner onboarding at scale
Business partners—brokers, franchisees, agents, service providers, and more—often sit outside the traditional HR or identity processes. Their access is typically managed through a patchwork of emails, spreadsheets, and tickets, often owned by the business rather than IT.
These manual workflows not only slow things down—they introduce risk and make oversight difficult. When partners help drive revenue, delays in onboarding hurt the business. And when their access goes unmanaged, they become a serious threat vector.

Manage the full non-employee lifecycle with automation and control
Contractors, partners, seasonal staff, and other third-party workers often follow inconsistent processes for onboarding and offboarding. Manual steps like spreadsheets, emails, and tickets slow things down, create compliance gaps, and leave lingering access when assignments end.
With automated lifecycle management, you can accelerate onboarding, support bulk hires, enforce expiration dates, and securely offboard non-employees — all aligned to your business processes. The result: faster productivity, reduced risk, and stronger oversight across every relationship.
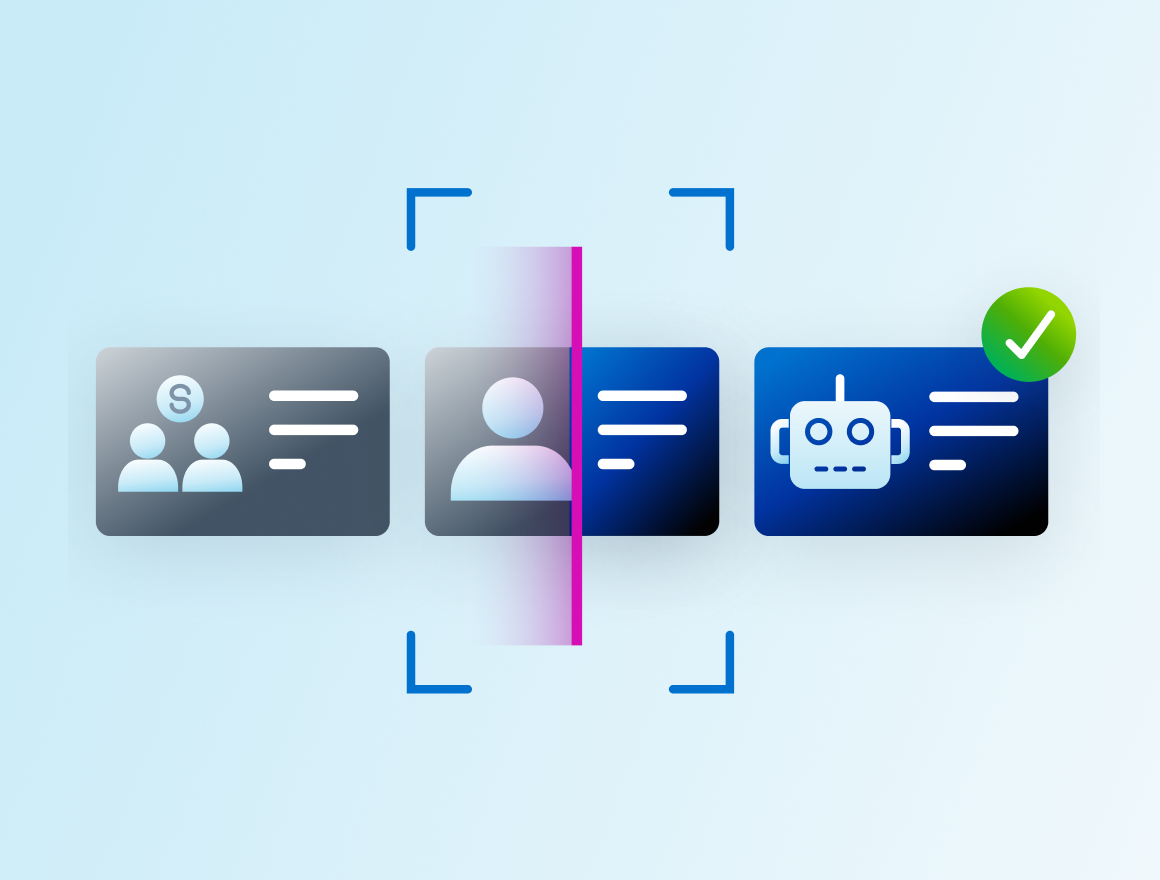
Ensure accuracy and oversight for every non-employee identity
Maintaining precise, up-to-date records for contractors, vendors, and other third-party users is critical to data security and operational integrity. Automated identity lifecycle management eliminates duplicate and inherited accounts, streamlines credential checks, and aligns access with active assignments—so you always know who has access to data and why.
With policy-driven triggers, you can easily schedule reverification for high-risk or long-term roles, ensuring timely updates as responsibilities change. This approach not only simplifies compliance but also keeps your security posture strong across the entire non-employee base.
See SailPoint in action
Explore on your own
Take a self-guided tour of SailPoint's identity security platform
Take product tourRelated resources
More about identity security for non-employees
Suites
Start your identity security journey today
SailPoint Identity Security Cloud enables organization to manage and secure real-time access to critical data and applications for every enterprise identity with an intelligent and unified approach.
Compare suitesAdvanced Capabilities
Take your identity security solution even further
The SailPoint Identity Security Cloud delivers the essentials for most organizations. SailPoint also offers advanced capabilities for specific needs.
INDUSTRY INSIGHTS
Related industries
Healthcare
Secure third-party access across providers, vendors, and partners—without slowing down patient care.
Learn moreGovernment agencies
Secure contractor and supplier access with a FedRAMP and StateRAMP-authorized solution built for public sector needs.
Learn moreManufacturing & supply chain
Control third-party access across facilities and supplier networks while keeping operations running smoothly.
Learn morefaq
Frequently asked questions
What is a non-employee?
A non-employee is any individual or organization that needs access to your systems, data, or applications but is not on your full-time payroll. This includes contractors, vendors, consultants, franchisees, business partners, agents, affiliates, interns, and temporary workers.
Non-employees are often referred to using different terms—such as third parties, external identities, B2B users, guest accounts, or partner IAM. While the language may vary by industry or region, all these terms point to the same challenge: governing users who fall outside of traditional HR-managed systems.
What is third-party risk?
Third-party risk refers to the potential for data breaches, compliance violations, or operational disruption caused by external users, such as vendors, contractors, and partners, who have access to your systems. These identities often lack formal oversight or consistent processes, making them more vulnerable to mismanagement, excessive access, and potential exploitation by attackers.
How does Non-Employee Risk Management improve security?
Non-Employee Risk Management strengthens your security posture by bringing structure, visibility, and control to third-party access. It applies Zero Trust principles to enforce consistent guardrails across every stage of the non-employee lifecycle — from onboarding to offboarding. The solution automates access approvals, triggers timely deprovisioning, and supports periodic revalidation of assignments. Security teams gain clear insight into who has access, what they can reach, how long they’ve had it, and why — making it easier to reduce standing access and close critical risk gaps before they can be exploited.
Does Non-Employee Risk Management support identity proofing?
Yes. The solution integrates with identity verification providers to verify third-party users before granting access. This ensures that contractors, vendors, and other non-employees are who they claim to be, which adds an important layer of trust and compliance to your onboarding process and reducing the risk of fraud or unauthorized access.
Why do organizations need a purpose-built solution for non-employees?
Non-employees often follow different onboarding paths, access timelines, and ownership models than employees. Their identities are typically managed through informal methods like spreadsheets or email threads, which increases security and compliance risk. A purpose-built solution ensures external identities are governed with the same rigor as employees, while accounting for the nuances of how the business works with outside parties.
Why is it important to audit third-party access?
Third parties often have access to sensitive data or critical systems but are less visible than employees in day-to-day operations. Regularly auditing their access helps identify excessive permissions, dormant accounts, or access no longer tied to a valid business need. Without this oversight, organizations face increased risk of insider threats, compliance violations, and security breaches.
What’s the difference between terms like partner IAM, B2B identities, external users, and guest identities?
These terms are often used interchangeably, but they all refer to the same core challenge: managing identities that exist outside your full-time workforce.
- Partner IAM typically refers to identity and access management for business partners and third-party collaborators.
- B2B identities highlight the organization-to-organization nature of the relationship (e.g., vendors or suppliers accessing your systems).
- External identities is a broad term encompassing any non-employee, including individuals or organizations.
- Guest identities are often short-term users with limited access—such as a visiting consultant or project-based contractor.
Despite the naming differences, they all point to the need for a dedicated solution that governs access across third parties securely and at scale.


