While authentication and authorization are often used interchangeably, they are separate processes used to protect an organization from cyber attacks. As data breaches continue to escalate in both frequency and scope, authentication and authorization are the first line of defense to prevent confidential data from falling into the wrong hands. As a result, strong authentication and authorization methods should be a critical part of every organization's overall security strategy.
Understanding authentication vs authorization
In the digital world, authentication and authorization are used in concert for identity-based security. Authentication verifies that users are really who they represent themselves to be. Once this has been confirmed, authorization grants the user permission to access different levels of information and perform specific functions depending on the rules established for different types of users.
Which comes first, authorization or authentication?
Authentication always precedes authorization in the access control process. It is essential to first confirm the identity of a user before determining their privileges.
Once the identity is verified, the next step is authorization, which grants or restricts access to resources and data based on predefined security protocols. Without the initial step of authentication, authorization workflows could unintentionally allow unauthorized individuals access to sensitive data, potentially leading to security breaches.
Importance of access control
Access control encompasses both authentication and authorization. It enforces rules that restrict or permit connections based on identity verification and permission levels. Together, access control, authentication, and authorization ensure that only authorized entities gain appropriate access to network resources and sensitive information. This not only ensures that data and networks are protected but also provides the identity management controls required to meet compliance requirements for regulations and standards.
What is authentication?
Authentication is the process of verifying the identity of a user, device, or application to ensure they are who they claim to be before granting access to systems, networks, or data. It is used to maintain security and privacy by ensuring that only authorized users can access resources.
Types of authentication
While user identity has historically been validated using the combination of a username and password, today's authentication methods commonly rely upon three classes of information:
- What you know
Most commonly, this is a password. However, it can also be an answer to a security question or a one-time personal identification number (PIN) that grants users access to just one session or transaction. - What you possess
This could be a mobile device or app, a security token, or a digital ID card. - What you are
This is biometric data such as a fingerprint, retinal scan, or facial recognition.
Common authentication methods include:
- Passwords
The most basic authentication method involves a secret string of characters known only to the user - Biometric authentication
Uses unique biological traits, such as fingerprints, facial recognition, and retina scans, to verify a user's identity - Token authentication
Uses physical or digital tokens, such as hardware keys or one-time passwords to authenticate users - Certificate-based authentication
Relies on digital certificates issued by trusted certificate authorities (CAs) - OAuth
Provides limited access to resources via tokens without exposing user credentials as part of authorization processes - Passwordless authentication
Replaces passwords with biometrics, magic links, or hardware tokens
These types of information are often combined using multiple layers of authentication or multi-factor authentication. For example, a user may be asked to provide a username and password to complete an online purchase. Once that's confirmed, a one-time pin may be sent to the user's mobile phone as a second layer of security. By combining multiple authentication methods with consistent authentication protocols, organizations can ensure security as well as compatibility between systems.
How authentication works
The specifics of how a user is authenticated vary, but all methods follow the same process. The authentication process includes three core steps:
- Credential Submission
Users provide credentials (i.e., an agreed piece of information shared between the user and the system) to prove their identity. - Credential verification
The system validates credentials against a trusted database or identity provider. - Access decision
Access is granted or denied based on credentials being validated.
What is authorization?
Authorization is the process of determining what resources, actions, or data a verified user or device is permitted to access after they have been authenticated. It is used to define and enforce the scope of access based on a user's identity and is controlled by predefined policies and permissions. Authorization permissions and policies can be applied to individual users or groups and include controls related to accessing files, executing commands, and using services.
Types of authorization
Authorization controls ensure users can access the data they need and perform specific functions such as adding or deleting information—based on the permissions granted by the organization. These permissions can be assigned at the application, operating system, or infrastructure levels. The following are the main types of authorization methods.
Role-based access controls (RBAC)
RBAC gives users access to information based on their role within the organization. By assigning permissions according to each person's role, organizations can ensure every user is productive while limiting access to sensitive information.
Attribute-based access control (ABAC)
ABAC grants users permissions on a more granular level than RBAC using a series of specific attributes, such as the user's name, role, organization, ID, and security clearance. It can also include environmental attributes (e.g., the time of access, location of the data, and current organizational threat levels) and resource attributes (e.g., the resource owner, file name, and level of data sensitivity).
Relationship-based access control (ReBAC)
ReBAC grants access to resources according to the relationship between entities, such as users, resources, and objects. It evaluates access requests based on contextual relationships (e.g., ownership, collaboration, membership, and friendship. It is widely used for environments like social networks, collaborative platforms, and zero trust architectures where access decisions need to adapt continuously to changing relationships and contexts.
Mandatory access control (MAC)
MAC manages authorization at the operating system level, governing threads and processes and which files and memory objects can be accessed. With MAC, security labels and categories are applied to assets to control which users or systems have access to them based on their level of sensitivity.
Discretionary access control (DAC)
DAC gives resource owners the authority to grant or restrict access to their resources at their discretion. Permissions are assigned based on user identities or groups.
How authorization works
Authorization uses various methods, such as those noted above, to determine and enforce permissions. While each has unique processes, the main steps for authorization, following authentication, are:
- Authorization request to access a particular resource.
- Access control evaluation to determine whether the user can access the requested resource.
- Authorization decision to grant or deny a user's request.
- Activity logging to what was done.
- Revoking permissions based on a change in a user's status or policies.
Authentication vs authorization: Key differences
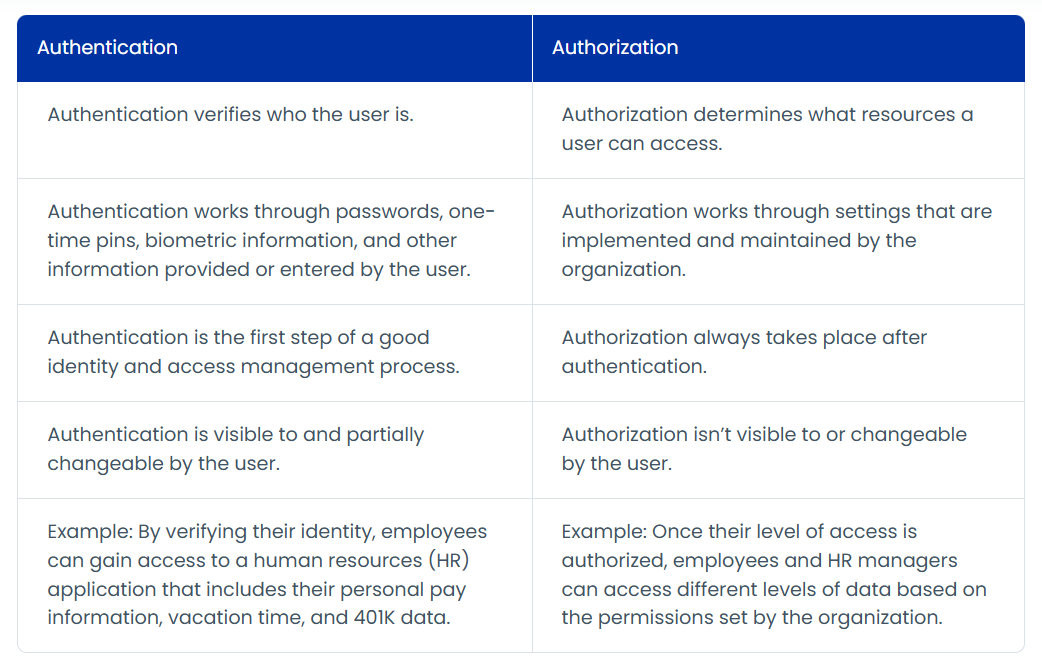
The fundamental difference between authentication and authorization is that authentication is the process of verifying who someone is. In contrast, authorization is the process of verifying what specific applications, files, and data a user is authorized to access. For example, a user can be authenticated as a company employee but needs authorization to access sensitive files.
Authentication vs authorization: Key similarities
Authentication and authorization are both core components of access control systems: 9dentity-centric processes that rely on credentials or attributes to verify users and determine their access permissions.
- Security and access control: Authentication and authorization secure access to systems, networks, and data from unauthorized access.
- Zero trust: Authentication and authorization continuously verify identity and enforce granular policies to ensure only legitimate, authorized access to resources.
- Identity: Authentication and authorization use identity information to make decisions about who can access what resources and perform what actions.
- Policies: Authentication and authorization use policies (e.g., RBAC or ABAC) for decision-making.
- Implementation frameworks: Authentication and authorization often utilize similar frameworks and protocols (e.g., Security Assertion Markup Language (SAML) and Open Authorization (OAuth)) to manage user credentials and permissions securely.
Real-life examples of authentication and authorization
Authentication vs authorization functions depend on the use cases. The following real-world examples show the differences between how authentication and authorization are commonly used.
Healthcare systems
Healthcare organizations must secure protected health information (PHI) to ensure compliance with regulations, such as the Health Insurance Portability and Accountability Act (HIPAA). Authentication and authorization processes are both key parts of the security processes that are used.
Authentication in healthcare systems
Authentication methods commonly used to protect healthcare systems, such as electronic health records (EHR), include credentials (i.e., usernames and passwords), smart cards, biometric authentication, and multi-factor authentication (MFA). For example, an authentication platform is often used to provide fast and secure access to EHR systems, while healthcare provider staff uses passwords, tokens, and biometrics for MFA.
Authorization in healthcare systems
Authorization tools, such as RBAC and ABAC, are used to ensure that only authorized users can access PHI or EHR systems. For example, doctors are granted access to all patient records, while receptionists' access is limited to basic contact information and required services (e.g., types of lab tests).
Online retail and digital marketplaces
Authentication and authorization processes are used to secure online transactions and customer data. This helps organizations meet compliance requirements for standards and regulations.
Authentication in online retail and digital marketplaces
E-commerce platforms require secure authentication to protect customer data and prevent unauthorized transactions. For example, online retailers use multi-factor authentication (MFA) and single sign-on (SSO) solutions to secure customer logins.
Authorization in online retail and digital marketplaces
For online retail and digital marketplaces, authorization systems allow for granular configurations to manage user privileges. Online retailers use authorization tools and processes to control what users can do, such as browsing products, making purchases, or managing their profiles. In online marketplaces, authorization tools and processes are used to provide sellers privileges, such as managing listings and viewing sales reports.
Streaming services
Streaming platforms rely on authentication and authorization to secure user accounts and ensure appropriate access to paid content. Additionally, authentication and authorization help these platforms meet requirements for restricting access to certain content based on a user's age.
Authentication in streaming services
Streaming tools use authentication tools, such as access gateways and single sign-on (SSO) solutions, to ensure authorized access to media. Multi-factor authentication (MFA) is also used to provide additional layers of security.
Authorization in streaming services
Authorization in streaming services is mainly based on subscription plans. Users can access content according to their subscription tier (e.g., Basic, Standard, and Premium).
Collaborative platforms (e.g., team communication tools)
Protecting users' privacy and sensitive information is critical for collaboration tools. Authentication and authorization are used to control access to systems and the data collected in them.
Authentication in collaborative platforms
Collaboration platforms implement various authentication mechanisms, especially in enterprise settings. The most commonly used are single sign-on (SSO) and multi-factor authentication.
Authorization in collaborative platforms
Role-based authorization is widely used for collaborative platforms. Permissions are often granted based on roles, such as admin, member, or guest. Administrators configure role-based access controls to restrict guests from accessing sensitive channels.
Content management tools
Content management systems (CMS) are used to create, manage, and publish digital content, such as websites, blogs, and documents. Authentication and authorization are used to control access to these systems and what different users are authorized to do.
Authentication in content management tools
Content management tools require robust authentication to prevent unauthorized access to certain functions, such as editing or deleting content. Authentication mechanisms are used to provide secure login processes and prevent brute force attacks.
Authorization in content management tools
Role-based authorization is used with content management tools to provide granular control over what users can access or modify. Typical roles include admins, editors, authors, and subscribers.
Financial services
Financial services, such as banking, credit cards, and investment platforms, rely on authentication and authorization to protect users' privacy and sensitive information. Authentication and authorization are part of compliance requirements for a number of regulations, including the Gramm-Leach-Bliley Act (GLBA), Payment Card Industry Data Security Standard (PCI-DSS), Sarbanes-Oxley Act (SOX), Financial Industry Regulatory Authority (FINRA), and Bank Secrecy Act (BSA).
Authentication in financial services
Financial institutions implement authentication mechanisms to ensure that users verify their identity. Multi-factor authentication (MFA) is a standard that often incorporates biometric authentication or hardware tokens.
Authorization in financial services
Authorization policies and tools are used to enforce what users can do within their accounts, such as viewing balances, transferring funds, or setting up automatic payments. Financial institutions implement fine-grained authorization policies to restrict sensitive transactions based on user roles and approval workflows.
Email accounts
Corporate email systems use authentication and authorization to protect users' email accounts. Authentication and authorization tools and processes play a vital role in safeguarding email accounts from authorized access and cyber attacks, such as phishing.
Authentication in email accounts
Authentication methods include single sign-on (SSO), credential-based authentication, and biometric verification, which are commonly used to protect email accounts. Multi-factor authentication has been widely adopted to mitigate risks from phishing and other social engineering attacks.
Authorization in email accounts
Authorization policies determine what users can do within the email system, such as sending, reading, and deleting emails, or accessing shared mailboxes. System administrators also use authorization policies to restrict access to confidential email folders or send company-wide messages.
Social media platforms
Social media platforms implement authentication and authorization mechanisms to protect user accounts and ensure appropriate access to features. These tools also help them adhere to certain compliance requirements for privacy and data protection.
Authentication in social media platforms
Most social media platforms offer users options for authentication. The most common is logging in with credentials, which sometimes requires multi-factor authentication. OAuth is widely used for social media authentication to provide users with a secure and convenient way to log in to various applications without sharing their passwords. It is also used to allow users to authenticate to third-party apps, such as websites, mobile apps, and collaborative platforms, through social media accounts.
Authorization in social media platforms
Authorization governs what users can do within the platform, such as posting content, managing groups, or accessing private messages. Social media platforms implement role-based and attribute-based access controls to differentiate permissions for standard users, moderators, and administrators.
Cloud storage
The broad adoption of cloud storage and the sensitive information that it holds makes it a target for cybercrime. Authentication and authorization are critical parts of cloud storage security.
Authentication in cloud storage
Cloud storage services use authentication to verify user identities and protect stored data. Common authentication methods include passwords, multi-factor authentication (MFA), single sign-on (SSO), and biometric verification.
Authorization in cloud storage
Authorization tools and processes are used to determine who can read, modify, delete, or share files within the cloud storage platform. Within organizations, granular permissions are applied to control user access based on roles, ensuring only authorized personnel can view, modify, or share critical documents.
A strong authentication and authorization strategy is essential
A sound security strategy requires protecting one's resources with both authentication and authorization. With a strong authentication and authorization strategy in place, organizations can consistently verify who every user is and what they have access to do—preventing unauthorized activity that poses a serious threat. By ensuring all users properly identify themselves and access only the resources they need, organizations can maximize productivity while bolstering their security at a time when data breaches are robbing businesses of their revenue and their reputations.
DISCLAIMER: THE INFORMATION CONTAINED IN THIS WEBPAGE IS FOR INFORMATIONAL PURPOSES ONLY, AND NOTHING CONVEYED IN THIS WEBPAGE IS INTENDED TO CONSTITUTE ANY FORM OF LEGAL ADVICE. SAILPOINT CANNOT GIVE SUCH ADVICE AND RECOMMENDS THAT YOU CONTACT LEGAL COUNSEL REGARDING APPLICABLE LEGAL ISSUES.
